Anthem
https://tryhackme.com/room/anthem
Enumeration
nmap -A -p- -v -sC anthem.thm -PnNmap scan report for anthem.thm (10.10.195.74)
Host is up (0.057s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Anthem.com - Welcome to our blog
| http-robots.txt: 4 disallowed entries
|_/bin/ /config/ /umbraco/ /umbraco_client/
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=WIN-LU09299160F
| Issuer: commonName=WIN-LU09299160F
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-01-24T16:01:28
| Not valid after: 2024-07-25T16:01:28
| MD5: 5220:dea9:3d1f:723c:ac00:2e5c:c137:d1ed
|_SHA-1: b965:4879:418e:3399:dd81:7de2:133c:0f12:0d84:c602
|_ssl-date: 2024-01-25T16:09:09+00:00; -2s from scanner time.
| rdp-ntlm-info:
| Target_Name: WIN-LU09299160F
| NetBIOS_Domain_Name: WIN-LU09299160F
| NetBIOS_Computer_Name: WIN-LU09299160F
| DNS_Domain_Name: WIN-LU09299160F
| DNS_Computer_Name: WIN-LU09299160F
| Product_Version: 10.0.17763
|_ System_Time: 2024-01-25T16:09:04+00:00
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=252 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -2s, deviation: 0s, median: -3s
TRACEROUTE (using port 3389/tcp)
HOP RTT ADDRESS
1 56.24 ms 10.18.0.1
2 57.77 ms anthem.thm (10.10.195.74)
NSE: Script Post-scanning.
Initiating NSE at 11:09
Completed NSE at 11:09, 0.00s elapsed
Initiating NSE at 11:09
Completed NSE at 11:09, 0.00s elapsed
Initiating NSE at 11:09
Completed NSE at 11:09, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 130.19 seconds
Raw packets sent: 131245 (5.780MB) | Rcvd: 120 (5.376KB)












Info
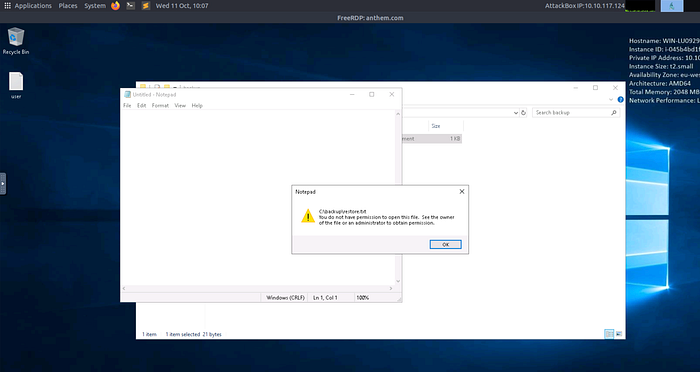
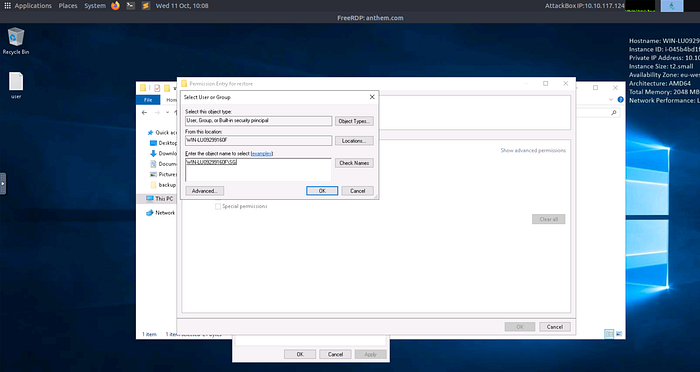
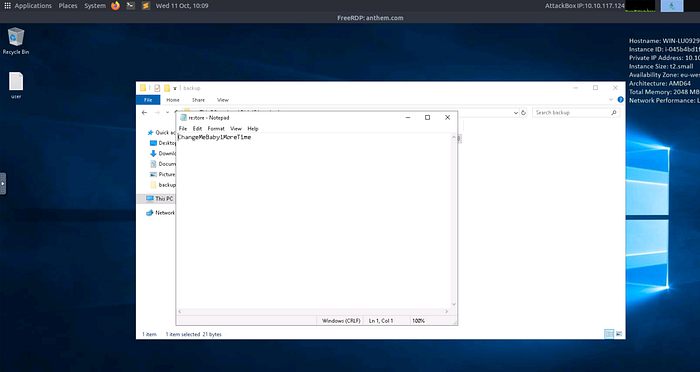
Privilege Escalation

Last updated
